Protect Kids on the Internet
Computers are wonderful learning tools, but they can also expose children to dangers like unwanted content and inappropriate contact from adults through the Internet.
Parents, educators and caregivers can limit the danger and protect kids on the internet. By protecting their personal information and being cautious about what they view, families can reduce their risks.
Set rules. Know what your kids are doing. Talk to them about the dangers.
How Parents Can Help
You don’t have to become a computer expert. Help is available from your Internet Service Provider, law enforcement, child safety organizations and the Attorney General’s office.
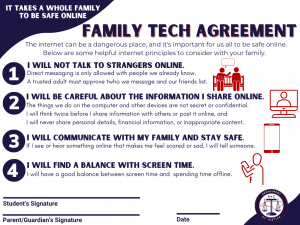
View NCDOJ’s Family Tech Agreement here.
Spend time with your kids, offline and online.
Get them to show you what they do on the computer, and the websites they visit. Discourage children, especially young children, from communicating with anyone online that they don’t know in real life.
Monitor your kids while you teach them Internet safety.
Some parents may feel uncomfortable checking on their child’s computer activities. However, experts say parents need to know what their children are doing online. It isn’t snooping, it’s caring.
Prevent inappropriate content.
The Internet is home to many images that are inappropriate for children. Young people sometimes seek out sexual material online, but some encounter inappropriate material unintentionally. Sexual material can appear in search results, or arrive by unsolicited email, known as spam, as an attachment or link. Teach children never to click on a link in an unsolicited email, and to close out of inappropriate content quickly. Use a child-friendly search engine to help them avoid inappropriate search results.
Help them “Keep it Clean.”
If you decide your teen is old enough to join a social networking site or have a personal web page, help them develop good standards for online behavior. Adults who want to exploit young people look for racy photos and postings. Make sure there’s nothing on your teen’s page to attract their attention.
Report the Wrongdoers.
It is a violation of federal law to knowingly send or attempt to send obscene material to a child under the age of 16. Report incidents to the National Center for Missing & Exploited Children at 1-800-THE-LOST (1-800-843-5678) or www.cybertipline.com.
Request a Presentation.
The Attorney General’s staff offers Internet education and safety programs.
Parents and friends can watch for warning signs that a child is at risk of being exposed to the wrong people or content.
Is Your Child At Risk Online?
Your child spends large amounts of time online, especially at night.
Child predators can be online at any time, but most work during the day and spend their evenings online trying to strike up conversations with young people.
You find pornography on your child’s computer, phone or storage device.
Adults who are seeking to exploit children often supply potential victims with pornography as a means of opening sexual discussions and for seduction. They may even use child pornography to try to show that sex between children and adults is “normal.”
Your child receives phone calls from someone you don’t know or is making calls, sometimes long distance, to numbers you don’t recognize.
Adults who want to exploit children use these calls to learn more about the children they are pursuing. Through Caller ID they may be able to determine the child’s full name and address. Child predators have been known to provide toll-free numbers so potential victims can call without their parents finding out. Phone conversations may include “phone sex,” often as a prelude to a face-to-face meeting for real sex.
Your child receives mail, gifts or packages from someone you don’t know.
As part of the “grooming” process that is used by child predators, it is common for them to send letters, photographs and gifts to their potential victims.
Your child hides what they are doing on the computer.
When a child turns the computer monitor off or quickly changes the screen on the monitor, they are attempting to conceal something. A child looking at pornographic images or having sexually explicit conversations does not want you to see it on the screen.
Your child becomes withdrawn from the family.
Adults who are seeking to exploit children work hard to drive a wedge between a child and their family. Any problem that a young person has at home can be manipulated to make that child feel isolated from his or her loved ones. Children under the influence of a predator may pull away from their families and may also become withdrawn after they have been victimized sexually.
Your child is using another email account.
Some online entities offer free email services, so email accounts can be created quickly and without cost. If your child is using an account other than the one you may have authorized, he or she may be communicating with someone who wants to keep the relationship secret. Keep in mind that your child could still meet and exchange messages with an adult while online at a friend’s house, the library or at school.
Source: Federal Bureau of Investigation
Request a Presentation
The Attorney General’s staff offers Internet education and safety programs.
Talk to Your Child About Internet Safety
Like the world itself, the online world is both wonderful and occasionally dangerous. When it is time for them to learn how to use the Internet safely, take time to talk to your children about:
- Causing legal or financial harm to the family if you “click” without getting permission.
- Exposure to harmful material (violent or sexually explicit scenes).
- People online who may start off friendly but then change.
Fear of losing their Internet access, mobile phone or gaming device keeps most children from telling their parents when they encounter something online that makes them uncomfortable. Ask your child to tell you when anything questionable happens to them online. Make it clear that you want to help, and that they won’t be punished if they tell you.Encourage them to tell you when:
- Someone they don’t know tries to communicate with them.
- An inappropriate site comes up on the screen.
- Someone harasses or threatens them online.
Teach your children about the differences between “pretend” and reality on the Internet. Many children like to pretend to be someone else while online. They feel anonymous, and sometimes take risks. Children need to understand that other people can also pretend to be someone else while online, and sometimes they do it to hurt people.
Children need to understand that real world rules and values apply on the Internet as they do in real life.
Don’t just tell your children what they can’t do. Make a point to sit with your children and see the sites they like to visit and the things they like to share online. If you think a site or a posting is inappropriate, explain why.
Make it clear to your children that you are in charge. Remind them that you have more experience dealing with the world.
Your children must understand that just as you decide which movies they are allowed to see, you will supervise their online activities.
With teenagers, strive to keep the lines of communication open. Teens are asserting their independence and learning to make their own decisions. It is normal for them to be interested in love and romance, and to seek adventure. But teen’s brains are not yet fully developed, and they are capable of making impulsive decisions without fully grasping the consequences of their actions. Some teens may need to hear in no uncertain terms that it is illegal and dangerous for a young person to have sex with an adult.
Finally, help teens “keep it clean” online. Adults who want to exploit young people look for teens whose online profile or posts indicate an interest in sex and teens who show a willingness to talk about sex online.
Request a Presentation
The Attorney General’s staff offers Internet education and safety programs.
Online Predators
Most online activity is harmless or even positive for young people. But adults who want to exploit them can use the Internet to try to locate and “groom” potential victims. You can minimize the risk of a young person meeting an online predator with some simple steps:
Consider When Your Child Can Go Online.
If you decide to let your child have an online profile or personal web page, your decision should be based on their age and maturity. Keep in mind that Facebook and Twitter don’t accept members under the age of 13.
Utilize Privacy Settings.
One of the best ways to protect your child and their privacy is to use a website’s privacy settings to control access to their profile page. Social networking sites often make changes to their privacy settings, so check frequently for changes or updates to the settings.
Monitor and Guide Online Behavior.
An adult who is looking for a young person to exploit will be drawn to a profile with entries or photos that show an interest in sex. A sexy profile and a willingness to talk about sex online with strangers are warning signs that require parental action. These online behaviors are much more likely to lead to sexual solicitation than posting personal information online.
Monitor Messaging.
Email, instant messages, texts… all of these can be used by young people to communicate immediately and secretly. Youngsters also use abbreviations to save keystrokes and keep parents in the dark.
Take Care of Photographs and Cameras.
Computers make it easy to send and share photographs, but it should be done carefully. Parents should monitor the use of digital cameras, cameraphones and webcams, which can be misused by young people.
Place Computer in a Common Area.
Place your computer in a central room of the house with the screen facing out so you can see it easily. Develop a list of family rules for using the Internet and post it next to the computer.
Keep Screen Names Anonymous.
Information in a screen names can be used to identify a child. Make sure that your child’s screen name does not include personal information such as real name, home address or school name.
Access Your Child’s Email.
Experts recommend that parents share an email account with their young child or maintain access to their child’s email account and check it frequently.
Remind Kids that Computer Use is Not Confidential.
Young people want to be treated as adults and may feel entitled to privacy. But they shouldn’t expect that everything they do on a computer is personal and confidential. And computers aren’t the only way kids go online. You’ll also need to keep an eye on how they use mobile devices such as phones and gaming systems.Some parents might feel that it is intrusive to monitor their child’s online activities, but a computer is different from a diary or a journal. A journal contains private thoughts that aren’t communicated to others. But emails, Facebook posts, Tweets, You Tube videos, online journals and instant messaging are an open window to your child’s life, carrying information to and from your home.
Request a Presentation
The Attorney General’s staff offers Internet education and safety programs.
Digital Imagery
Digital cameras and cell phone cameras have made it easy to take photographs. Unfortunately some young people misuse this technology. When young people engage in “sexting” (taking and sharing sexual photos), it can do lasting harm.
How it happens:
Some inappropriate photos are taken for a current boyfriend or girlfriend, or to attract the attention of another young person. In some instances young people have been pressured or tricked into taking inappropriate pictures by another young person or an adult.
How it spreads:
After a teenage couple breaks up, the sexual photos may be shared and circulate widely throughout a school or peer group. Regardless of how or why it is created, once a digital image has been shared via any electronic media it is virtually impossible to retrieve. Nude or suggestive photos are routinely posted, traded, and sold. They can be altered and misused, and remain in circulation forever.
How law enforcement gets involved:
If a photo shows a minor engaged in sexually explicit conduct it may be treated as child pornography by law enforcement. Producing, possessing or distributing the photo could lead to criminal charges regardless of the original intent of the photographer. In addition, the young person’s parents or guardians may be questioned to determine if they knew about the photograph.
Videos, too:
In addition to misusing still photography, young people sometimes misuse webcams to transmit sexual images of themselves. Many experts believe the dangers and risks of webcam misuse outweigh any potential benefits for young people.
Young people often act on impulse. They don’t recognize the long-term consequences of actions like misusing digital images. Parents and guardians should exercise control over digital cameras, camera phones and webcams to make sure they are being used appropriately.
Computer Stalking & Bullying
If someone threatens your child with violence, contact law enforcement immediately. If your child is being threatened or harassed online, you may want to contact one or more of the following:
School Resource Officer:
Your child’s school may have a School Resource Officer (SRO), a sworn law officer, who can help. If so, let the SRO know about the harassment or threats. If your school does not have an SRO, contact local law enforcement.
Internet Service Provider:
Your email account settings or instant messaging software may allow you to block further messages from the sender. You can report the harassment or threats to your ISP and the harasser’s ISP if you know which one the harasser uses. You can ask that the harasser’s account be suspended or blocked.
CyberTipline:
If your child receives invitations for sexual acts or unsolicited obscene material over the Internet, you can report it by calling 1-800-THE-LOST (1-800-843-5678) or by visiting the CyberTipline.What to do
- Save the original message. Don’t delete or erase threatening emails or other communications from your mailbox or voicemail. If you are asked to share a threatening email message with law enforcement, forward the original message. A printed copy of the email or an excerpt from it will not be as useful to law enforcement as the original email message that you received.
- Don’t respond to messages from people you don’t know, and don’t engage in any communications with a harasser. Keep a note of the times and dates of abusive messages or incidents. If the harassment continues, consider contacting a victims’ rights group for advice and support.
Request a Presentation
The Attorney General’s staff offers Internet education and safety programs.
Safer Social Networking
Like adults, young people should protect their privacy and practice good behavior online. In addition, there are some extra precautions parents should take with their children to reduce risks.
Is your child ready?
Consider your child’s age and maturity level before you agree to let them join a social networking website. Facebook and Twitter, two of the most popular sites, ban youngsters under the age of 13. Google+ allows teens to join, but the network’s default privacy settings are more restrictive for young users. Remember, young users of social networking sites could be exposed to adult content.
Use privacy features.
Privacy features are a key element of safe social networking. If you allow your teen to join a site, make sure they use the available privacy features. Websites frequently change or update their privacy policies, so you’ll need to stay up-to-date on the site’s features.
If it is posted, it isn’t private.
Make sure your teen understands that the things they post online can easily end up being seen by people they never intended, no matter their privacy settings. If they want a photo or something they wrote to stay private, make sure they know it isn’t safe to post it anywhere online.
Keep it clean.
Talk to your teen about what kind of information is appropriate to share online. If a young person’s chat room conversations, online profile or blog entries suggest an interest in sex, an adult who is looking for a willing young person may believe that they have located a good candidate to victimize.
Who can be your “friend”?
Young people who are active online will receive “friend” requests from people they’ve never met. Talk to them about how to handle those requests. Make sure they know to think carefully before accepting requests from people they don’t know in real life.
Online-only friends need a special category.
If you allow your teen to make online friends with people they don’t know in real life, consider setting up a special group status for those people. You should be able to create one that doesn’t allow them the same access to your child’s information, and prohibits them from posting comments on your child’s page.
Most importantly, make sure your child knows to talk to you or another trusted adult if something happens to them online or in real life that makes them uncomfortable. If the cause of their discomfort was inappropriate content or abuse online, report it to the site immediately.
Parents who decide to let their child join a social networking site should learn how to make it a safer experience.
One way to help kids know what’s OK and what’s not is to set clear standards for using computers and other electronic devices like smartphones and tablet computers. You might want to consider:
- Telling young children to ask for your permission before they access the Internet.
- Setting time limits for computers and other devices, per day or per week, and what time of day is OK.
- Sharing your child’s first email account.
- Pre-approving your child’s list of “buddies” if you decide to allow them to use instant messaging, and requiring them to get your permission before adding any new names.
- Limiting your child to social networking sites that you approve, if you decide to allow them to use these kinds of sites.
- Joining social networking sites that your child uses, so you can monitor what they share.
Setting Family Computer Rules
Sample Family Rules
When possible, have your family computer rules in place before your children begin using the computer. Children find it easier to accept and obey rules that have already been established.
Once you’ve outlined those standards and your kids know what’s expected of them, you may want to create a list of clear guidelines that can be posted on your computer as a reminder.
View NCDOJ’s Family Tech Agreement here.
Using the computer is a privilege. In order to enjoy this privilege and use the computer, we agree to follow these rules:
- We get permission before accessing the Internet. On a shared computer, we use our personal login.
- We set a strong password for every device that can be password-protected, and we do not share our passwords with anyone but our parents.
- The things we do on the computer and other devices are not secret or confidential, and we do not hide what we are doing.
- We visit web sites that are appropriate for our age. We don’t visit web sites or access information that are “off limits” for us.
- We get permission before sending or posting photos or personal information.
- We get permission before downloading apps or making purchases online.
- We tell our parents about anything we see online or in a text message that makes us uncomfortable.
- We only use email accounts that our parents know about.
- We don’t enter chat rooms.
- Instant messaging is only allowed with people we already know. Our parents must approve the members of our “buddies list.”
- We don’t respond to messages from people we don’t know.
- If we are allowed to join social networking sites, we utilize privacy settings to control access to our page and we keep our settings up-to-date.
- Friends” are people we know in real life. People we only know online get limited access.
- We share our passwords with our parents so they can monitor our online activities.
- If we’re using a public Wi-Fi “hot spot,” we only surf online. We never enter account numbers, passwords, or any other information when using unsecured Internet access.
- We can use computers and other electronic devices between the hours of ______ and ______.
- We can use computers and other electronic devices for up to _______ hour(s) per day.
- These rules apply to our home computer and all other computers and electronic devices we use.
____________________ Name _____________________ Date